DIY insider threat presentation CS3sthlm – elaboration on questions received
During my presentation at the CS3sthlm conference (DIY insider threat detection/prevention within ICS environments), I’ve received some questions on this topic. Within this post I’ll elaborate a bit more on these.
A majority of the people in the audience claim they know their environments. Do you believe them?
The results of the poll during the presentation are shown in the following picture.
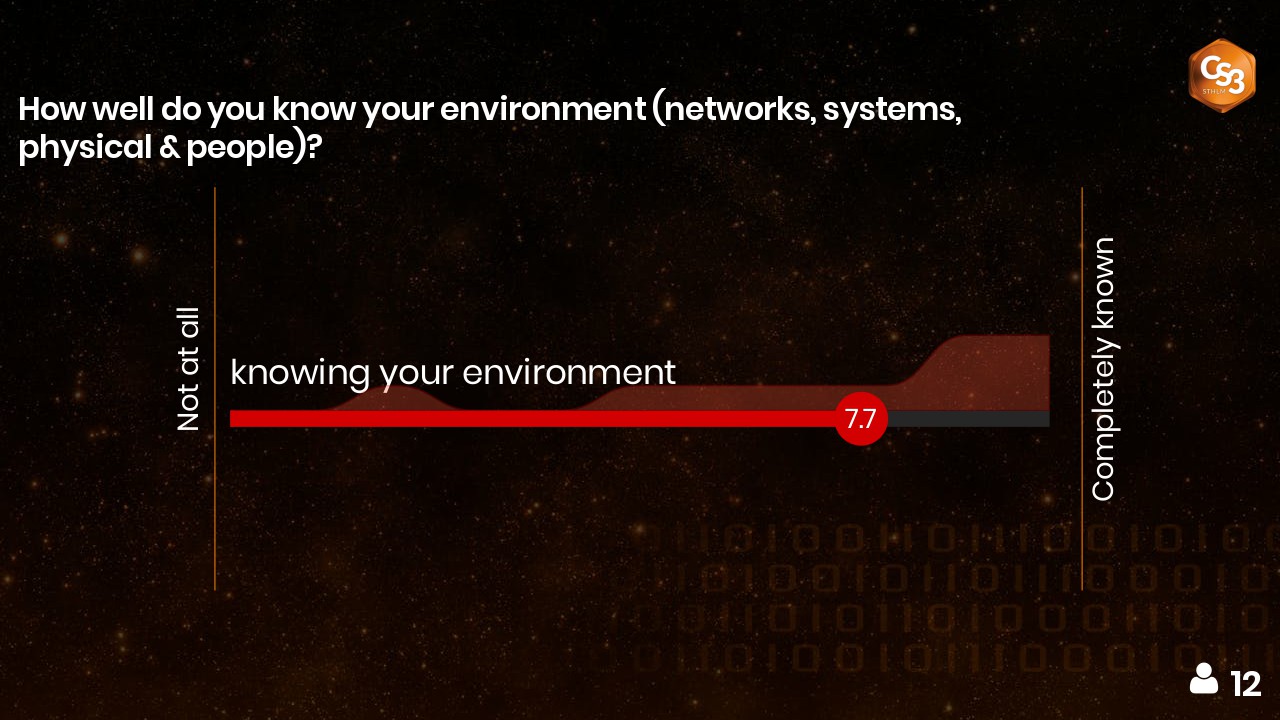
My answer to this question during the conference was: “I would like to challenge them.”
I still stand by that answer as I find it hard to believe that you can actually know your environment a 100% (as the picture shows some people must have answered “completely known”).
I actually asked a “tricky” question (at least in my opinion) as the environment I was referring to entails all network, system, physical and social assets (people working onsite).
You can do pretty good on the network, system and physical level, if you have created an actual baseline of these levels and if you followup on these quite often, but on the social level you might find out that you are still missing parts of the puzzle (also read DIY insider threat detection/prevention within ICS environments).
It is all too often that – during the ICS/SCADA/OT security assessments we do – we find out that there are still “invisible” parts in the network, that there are still systems within the environment that slipped through the “visible” maze and that there are still flaws within the physical security measures. It happens too often that insiders (being it employees, contractors or other types of insiders) go rogue and do harm to your environment.
Only if you do recurring security checks and verification of your environment, you can state that you know your environment rather well … until something (new) gets introduced within your environment during upgrades/maintenance/… but this should then be covered through a change management process.
But again, I would like to challenge those that said they know their environment pretty well. Challenging and verification of this is always good and will give you even a better insight to your environment as everybody looks at things from a different angle.
Does it makes sense to have monitoring as a service from MSS/MDR providers?
You can use MSS/MDR providers to facilitate the monitoring for you. However, you have to keep in mind that the chosen provider has to be included within your pool of insiders. This because they receive a certain access and right to see logs and events that originate from within your organisation.
Depending on the type of access that particular provider has, you also have to deal with Hidden dangers of remote management.
Should we worry more about insiders / internal attackers?
If you ask me, yes you should. Insider threats / internal attackers have been and will always be part of your risk posture. You should be ready to deal with these. Early detection of insider threat actors and deterring them as long as possible gives you more time to act on it and better protect your environment.