IEC62443, NIS2 and security testing – a happy marriage?
When the NIS2 EU Directive came into effect, I wondered what the implications would be for security testing in industrial environments. After all, a large part of the NIS2 directive focuses on supply chain and network security. In this article, I’ll highlight some aspects of NIS2, CER and IEC62443 and give my views on how they impact cybersecurity testing in industrial environments. This is NOT a full explanation of the previously mentioned directives or standards, there are other articles available if you are looking for that.
NIS2 impact on security testing
Looking at the 11 points mentioned in Article 21.2 of NIS2, which also states that “an all hazards, risk-based approach must be taken”, I’ll focus on the following 3 points in this article:
- (d) Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers;
- (e) Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure;
- (f) Policies and procedures to assess the effectiveness of cybersecurity risk-management measures;
In the context of supply chain security, Article 21.2 also states that “a vendor validation program shall be implemented,” which can be translated into the following key elements that should be part of such a vendor validation program:
- Establish security requirements to be used during the acquisition phase. Such security requirements can be based on IEC62443-2-4 (security requirements for vendors).
- Validating these requirements through paper-based assessments – this can also be part of a vendor selection process.
- Perform sFAT and sSAT (security fat and security sat) tests to verify that what is written on paper is actually implemented.
Articles 32 and 33 of NIS2 state that competent authorities will have the power to conduct security audits and scans, either on-site or off-site, performed by trained professionals. This will most likely be the case if a significant incident has occurred at your facility. In my experience and opinion, performing assessments in industrial environments is not something that should be done by anyone, and not without being careful about what you are doing. So, as the OT asset owner who knows your environment best, you should start performing audits and assessments yourself (or have a trusted party do so) if you have not already done so, to maintain control over what happens in your environment. These audit and assessment reports can then be used as evidence for regulators or authorities.
In terms of security testing and NIS2, the EU Directive results in the following mandatory things to have or do:
- Security testing policy, approach & execution – also see Assessment Services
- Performing risk assessments (criticality and maturity) within OT – also see Cyrias – conducting cybersecurity risk assessments
- Vendor validation (sFAT & sSAT) – also see Vendor Validation Services
- Incident management & handling policy & processes
CER resulting in Cyber HAZOP
If we also take into account the CER – Critical Entities Resilience (Directive 2022/2557), we can see in article 12 the following: “Within 9 months of receiving a notification, a risk assessment must be carried out if your organization is identified as a critical entity. And such a risk assessment must be carried out at least every 4 years. These risk assessments are not limited to logical, physical and human risks, but also include environmental risks, accidents, disasters, terrorism…”.
This also refers to the “all hazards, risk-based approach” mentioned in Article 21.2 of NIS2, but it also means that security should be included in all cyber risk assessments conducted, which may result in the need to conduct cyber HAZOP exercises. After all, there is “no security without safety, no safety without security”.
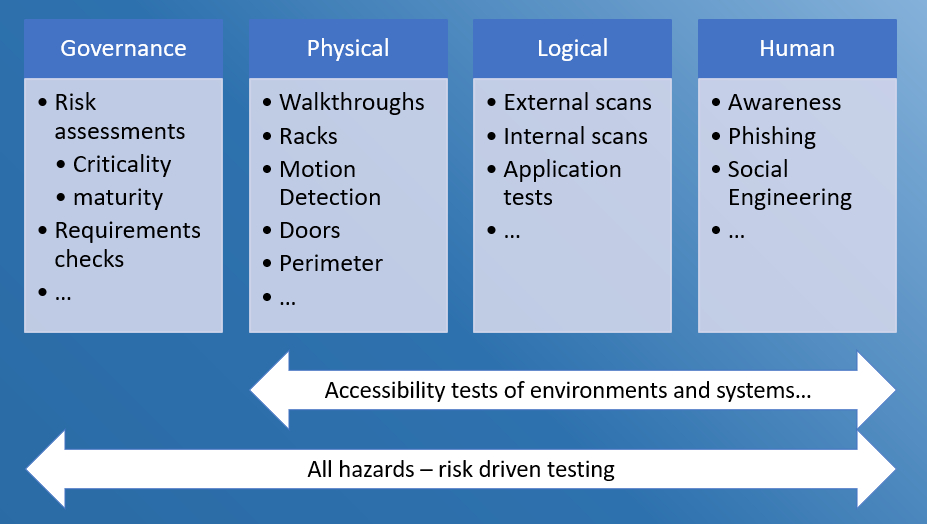
Cybersecurity testing program within OT
Considering all the necessary things, it is best to come to a cybersecurity testing program that covers all the necessary elements such as governance, physical, logical and human:
IEC62443, NIS2 and security testing – a happy marriage?
To answer our first question, are IEC62443, NIS2 and security testing a happy marriage? In my opinion, YES … BUT, as an asset owner, you should:
- Have/create/modify/implement a test strategy for OT environments
- Perform risk assessments (criticality & maturity)
- Have/create/modify/implement a Vendor Security Validation (including Security FAT & Security SAT) as part of your testing strategy
- Be prepared for the extra (testing) work & need for security budgets
- Document everything (approach & all test results)
Contact us to learn more about our vendor validation and risk assessment services.